DevSecOps
It's like DevOps, but your security team is a lot happier

Who am I?
Alistair Chapman
agc93
agc93

Cloud Security Engineer
.NET MVP
Red Hatter
Walking, talking case of impostor syndrome
The Plan
(likely going to be abandoned about 5 minutes in)
- Summary
- Why not agile security
- Integrating security controls
- Improving ops and response

Security and Devops
aka why is this so hard
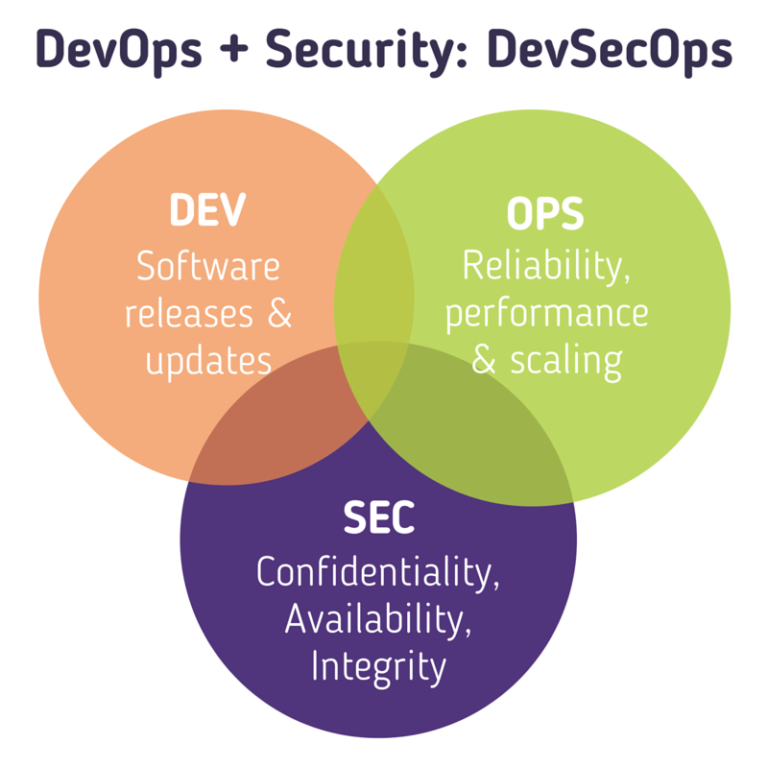

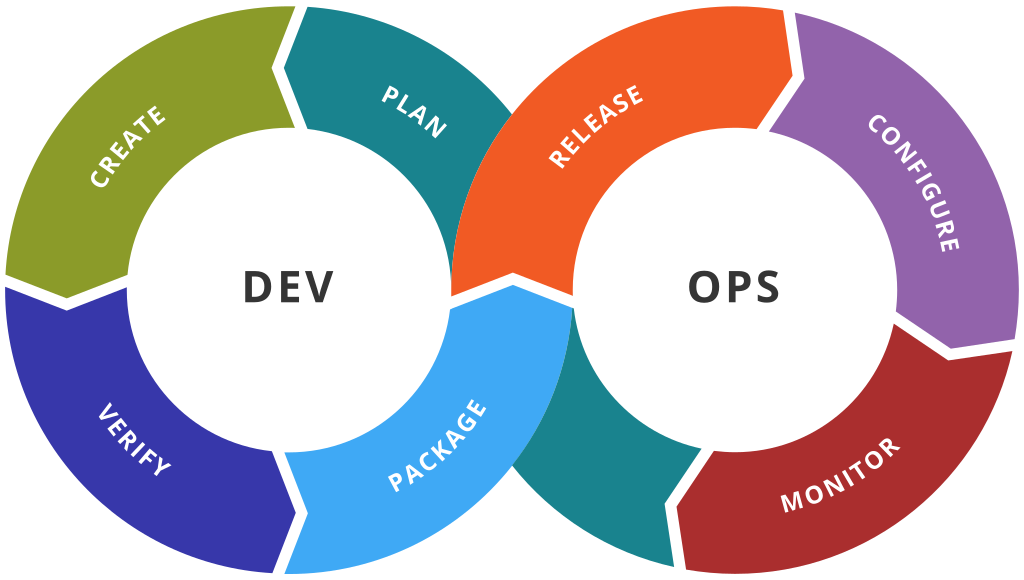
DevOps
The undefinable morass
Plan
- Security teams don't like surprises
- They might have more cross-functional concerns
- Involve them early and often
- InfoSec will have their own planning to do
Keep InfoSec informed
CREATE
- Use development tooling to improve security
- Enforce security standards just like you do code standards
- Track your dependencies!
Make the most of tooling
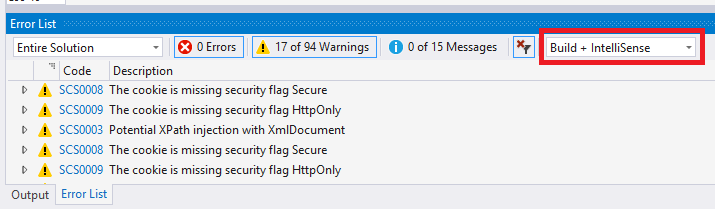
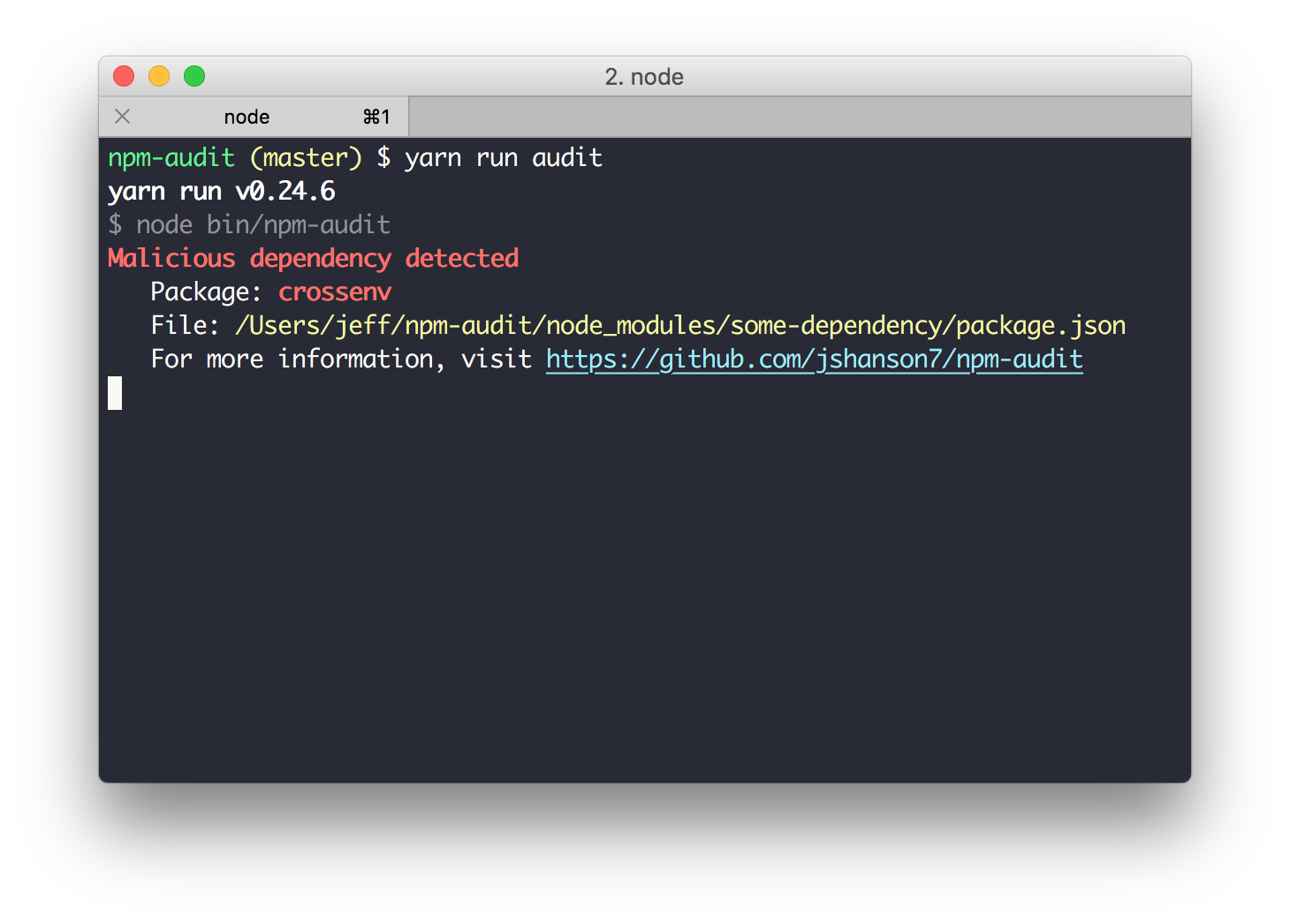
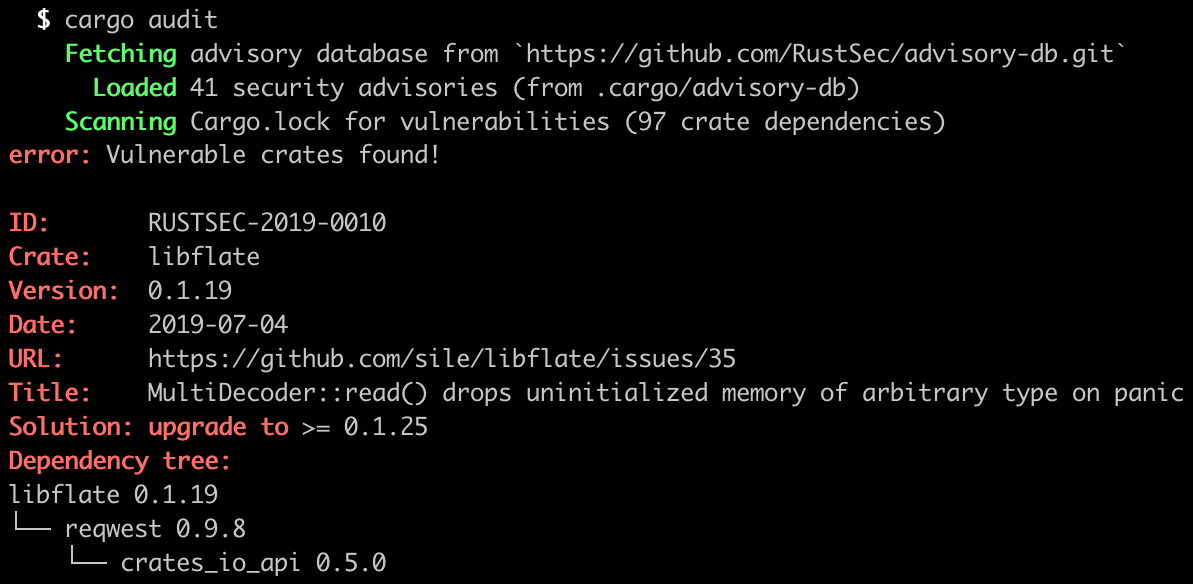
CREATE
- Enforce effective key and secret management during development!
- Use tools like git-secrets and gitleaks
- Provide developers with managed infrastructure
Make the most of tooling
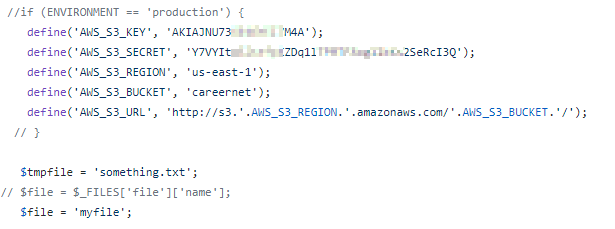
This took less than a minute to find!
VERIFY
- This is the first time to stop vulnerabilities
- Ensure there are processes for emergencies!
- Also a good opportunity for auditing/recording
- SAST/DAST/IAST/RAST/OAST
First line of defence

Package
- Always control and communicate package reach and status
- Effectively track code changes and package versions
- Particularly dependency changes!
- This will with improving testing outcomes and incident response
- DLP and release gating can help with enforcing boundaries
First chance to f*** it up
Release
- Release automation increases product risk
- Prepare for the worst case
- Sign anything you can
- Never release without the ability to hotfix
- Dogfood if possible
- Define clear streams and conditions
The big one

Configure
The best code can't save you here
Packaged Products
- Sensible defaults vs secure defaults
- No such thing as fast enough
- Use configuration to encourage best practices
(UN)Managed Services
- Document clear plans and comms for security
- No such thing as fast enough!
- Test your management infrastructure as well as your app infrastructure

Monitor
Metrics aren't just for performance
Tracking
- Log everything!
- Infrastructure should be monitored as well as apps
- Prioritize admin and auth
- Always baseline metrics
- Attackers will mess with logging!
Reporting
- Inform InfoSec early!
- Always have clear contacts, processes and protocols
- Inform InfoSec early!
- Remember legal obligations
- Inform InfoSec early!
Response
- Trust your security team!
- They will have existing response plans and processes
- Provide as much detail as you can
- Ensure the right people are available and aware
- Security incidents aren't always like other ops incidents!
- Need-to-know information
- Legal obligations
- Access to relevant events, logs and sensitive data
"Well, that's definitely bad"

Plan
- Treat security incidents like other ops incidents
- RCA
- Retrospective
- Process improvements
- Specific remediation controls
- Use lessons to improve product design
Learn from incidents

DevSecOps
Is it hard? Yes
Will it improve how you deliver software? Yes

or is it SecDevOps? DevOpsSec?
Alistair Chapman
@agc93
(essentially everywhere)
https://blog.agchapman.com/
https://github.com/agc93/
